How to avoid security issues in Composer dependencies
Composer is a great tool for requiring third party modules and software packages for your project. It’s an essential part of the current Magento 2 project structure.
Because of the possibility to add more and more modules it is also getting more and more difficult to keep track of relevant security updates. That is especially the case when required modules have further requirements.
Here are 3 tips how to improve your project’s security
1. Subscription of third party repositories (when using sticky version numbers)
If the applied module is published on Github you can subscribe to the repository. Github then informs you via email about changes of the code. If the email contains relevant information regarding security issues, the version of the required module can be increased in your project‘s composer.json file. For updating you just have to type:
composer update vendor/module
2. Avoid static version numbers
Compared to option 1 it would be much more safe to manage the applied parts and the own project via semantic versioning. In those cases you can define the dependencies as follows:
composer require vendor/module=~3.1
In this specific case you would get all versions between 3.1.0 and 3.2.0 by executing a “composer update”. If the vendor fixes the module, he just increases the version number at the third position and the new code will be applied and implemented with the next update.
If the vendor implements a new feature however, he increases the major or minor version, e.g. 3.2.x or 4.0.x. The code will only be applied by a manual action of a developer. Reviewing the code before committing the new version would be highly recommended.
3. Use SensioLabs Scanner
While option 2 is already a very cool and flexible solution, the developers of the vendors of the applied modules still need to be informed about the security issues and they need to fix them. But the moment they release a new version might be too late. As a developer, you definitely want to know about issues immediately, to disable or replace the dangerous module.
SensioLabs – creator of the Symfony framework – created a database containing known security issues of several packages (Magento, Shopware, Zend Framework etc.) and they allow you to get these information via an api or a cli client. These tools scan a given composer.lock file. For every current commit or tag they check for an entry inside the database. After processing the file you get a list of findings if there were any.
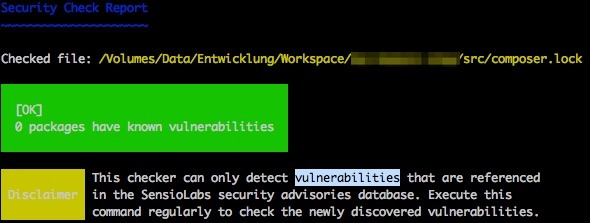
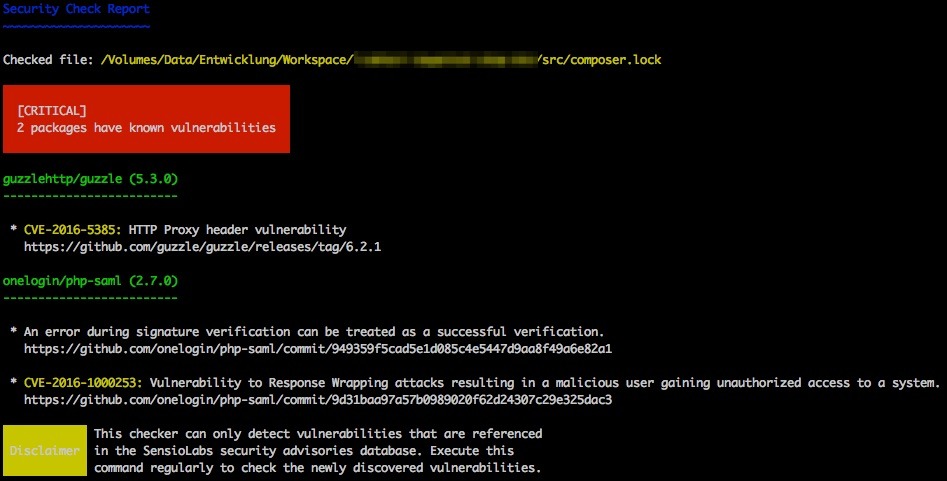
The client can be easily installed via Composer.
composer require sensiolabs/security-checker
Depending on your project and your required Symfony dependencies you might need to use a specific version of the tool.
To run it, all you have to type is:
vendor/bin/security-checker security:check
By today there’s only one entry for Magento 2 in this database:
Links
- SensioLabs security issue database: https://security.sensiolabs.org/
- SensioLabs security scanner: https://github.com/sensiolabs/security-checker
- Semantic versioning: https://semver.org/