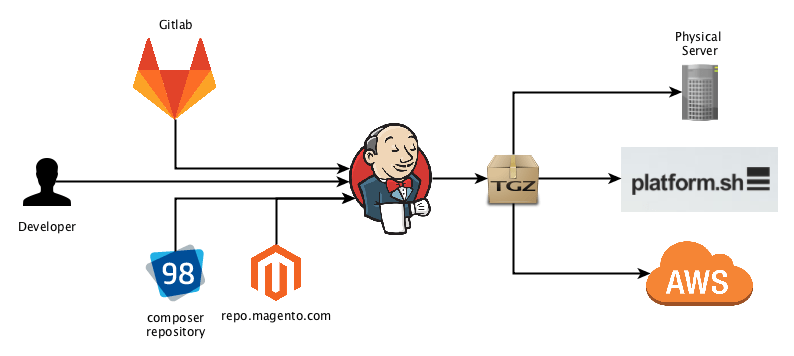
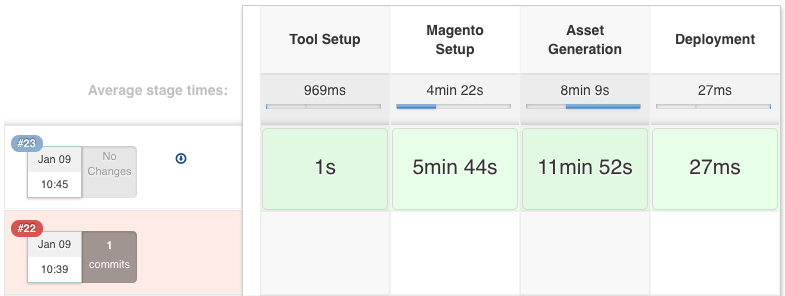
Nice to know: Install N98-Magerun via Composer
There is a so far merely undocumented installation procedure for Magerun that is extremely handy in project configurations. You just require Magerun within the Magento project and you can then execute it from the vendor’s bin folder: $ composer require n98/magerun2 […] $ ./vendor/bin/n98-magerun2 –version n98-magerun2 version 1.3.2 by netz98 GmbH Afterwards if you commit the composer.json and composer.lock files it is a take-away for the whole team. So it is regardless whether you’re running it locally, inside a docker…